how to hack locked wifi with laptop

Title: WiFi Password Cracking in 6 Minutes and 4 Seconds
Channel: Loi Liang Yang
WiFi Password Cracking in 6 Minutes and 4 Seconds by Loi Liang Yang
Unlock ANY WiFi: Laptop WiFi Hacking Secrets Revealed!
Unveiling the Wireless Web: Your Laptop’s Hidden WiFi Powers
Let's be frank: we all crave that sweet, sweet WiFi connection. Whether it's for streaming, working, or just staying connected, a stable internet connection has become essential to our lives. But imagine a world where access isn't limited. Wouldn't that be amazing? Well, grab your metaphorical hats. This article pulls back the curtain. We will explore the fascinating, and sometimes tricky, world of laptop WiFi. I’ll show you how your device, in the right hands, holds some surprising capabilities.
Decoding the Digital Signals: Understanding WiFi Fundamentals
Before diving into the finer points, let's get grounded. Think of WiFi as a secret language. Your laptop is the translator, deciphering signals broadcast by your router. These signals, you see, travel through the air as radio waves. They carry data, information, and, of course, the internet. So, it is essential to understand how these signals work. They are the key. The different channels and frequencies that your router uses become important. This will be crucial. Because, simply put, this lays the foundation. This fundamental knowledge is important.
Beyond Passwords: Exploring the WiFi Landscape
Now, let’s stretch our minds. Forget simple passwords. Let’s see beyond that. WiFi security relies on several protective layers. This includes protocols like WPA2 and WPA3. These are more powerful than older, outdated methods. But, these systems, while robust, are not completely invulnerable. Knowing that unlocks a new perspective. Also, consider the varying degrees of security. They depend on your router's settings. Also, the strength of your chosen password plays a role. So, understanding these layers is critical.
The Ethics of Exploration: A Word of Caution
Hold on a moment. Before you get too excited, let's talk about ethics. The intent of this piece is for informational purposes only. I must emphasize it. Accessing a WiFi network without permission is illegal. That's also morally wrong. I do not condone any form of unauthorized access. Always respect the privacy and security of others. This, indeed, is very important. This applies to all technological exploration.
Unlocking the Potential: Tools of the Trade
Okay, so we've established the rules. Fine. Let’s explore the tools. Laptop WiFi hacking tools exist. They can be quite powerful. Some freely available programs are used for network analysis. Others are used to test security vulnerabilities. They can even help you understand how WiFi works. Some of these tools are designed for penetration testing. They help identify weaknesses in a network's security. Always use these tools responsibly.
The Art of Network Analysis: Sniffing Out Information
Network analysis, in essence, is about observation. It involves capturing and examining data packets. This allows you to see the flow of information. You can also identify potential security risks. This requires specialized software. You will need to know how to interpret the data. Tools like Wireshark are often used. They allow you to capture packets. They then provide a detailed analysis of the data. The goal is to understand what is happening.
Cracking the Code: Password Recovery Techniques
Now, let's consider password recovery. Several techniques exist for this. These techniques are used under ethical situations only. This can be useful if you have forgotten your own password. Brute-force attacks try various combinations. These are automated attempts to guess passwords. Dictionary attacks use lists of common passwords. This is another approach. The success depends on the password complexity. Also, it relies on the security protocols being used.
Staying Secure: Defensive Strategies and Best Practices
How do you protect your WiFi? Well, there are several methods. First, use a strong, unique password. Your password should be at least 12 characters long. Second, enable encryption protocols, such as WPA3. This will help keep your data safe. Regularly update your router's firmware. This helps patch security vulnerabilities. Also, consider using a VPN. This adds a layer of protection to your internet traffic. Finally, always be vigilant. Be aware of potential threats.
The Future of WiFi: Evolution and Innovation
WiFi technology is constantly evolving. New standards are released. Speeds are increasing. Security protocols are also getting better. We can anticipate new methods of wireless communication. This could include the integration of artificial intelligence. We could see more advanced security measures. The future is bright for WiFi technology.
Conclusion: Mastering the Wireless World Responsibly
You have learned a lot. You now see that WiFi is complex. It is also fascinating. You understand how it works. You now understand the ethical responsibilities. You are now equipped with the knowledge to navigate the wireless world safely. Remember, the power of knowledge comes with responsibility. Embrace the learning, but always respect the laws. Practice ethical behavior. You will then go far in this exciting field.
Windows 10 WiFi Nightmare? FIX It NOW!Unlock ANY WiFi: Laptop WiFi Hacking Secrets Revealed!
Alright, future digital explorers! Let's dive headfirst into the intriguing world of WiFi – a world we’re all connected to, yet often misunderstand. Today, we're going to peel back the layers, revealing the secrets behind unlocking, or more accurately, understanding how WiFi security works, and the vulnerabilities that exist. We're talking about "WiFi hacking" secrets, but remember, our aim isn’t to break the law. It's all about ethical understanding and responsible digital citizenship. Think of this as an in-depth, hands-on tutorial, much like taking apart a watch to see how it ticks, not to steal its precious moments.
1. The WiFi Landscape: Your Digital Front Yard
Before we jump in, let's paint a picture. Your WiFi network is like your digital front yard. It's the space where your devices connect to the internet, and like any good front yard, there are fences (security protocols) and gates (passwords). Understanding these fences is the key to our journey. We're not talking about breaking down the gates, but rather learning to identify the weak points and why they exist. Consider WEP, WPA, and WPA2; these are the different types of locks you might find on that gate.
2. Deciphering the Encryption: Why Isn't WiFi Just Open?
Ever wondered why your WiFi isn't just an open door to the internet for everyone? Well, that's where encryption comes in. Encryption is essentially a code that scrambles your data, making it unreadable to anyone without the "key" (password). Think of it like a secret language only you and your devices understand. WEP, WPA, and WPA2 are the methods used to encrypt the data, and each has its strengths and weaknesses. WEP, for example, is like a flimsy padlock compared to WPA2, which is like a solid, modern deadbolt.
3. The Tools of the Trade: Software and Hardware
Now, let's talk about the toolbox. To truly understand WiFi security, you'll need some special tools. We're not talking about crowbars and lockpicks here – it's all about software. Programs like Wireshark (a network protocol analyzer – think of it as a detective's magnifying glass for network traffic) and Aircrack-ng (a suite of tools used for analyzing wireless networks) are essential. We're also talking about a WiFi adapter that can be put into "monitor mode," which allows it to 'listen' passively to the network around it.
4. Understanding Packet Sniffing: The Invisible Observer
One of the core concepts is packet sniffing. Imagine eavesdropping on a conversation; you'd be listening to packets of data being transmitted over the network. Packet sniffers like Wireshark allow us to do just that, but only with the permission (or ignorance, which is ethically wrong) of the network owner. We’re not spying; we're learning how networks communicate. This helps us see the raw data, the 'chatter' of the network, without interrupting its flow.
5. Cracking WEP: A Legacy Vulnerability
Remember that flimsy padlock? WEP is the archaic encryption protocol, and it's notoriously easy to crack. This is where tools like Aircrack-ng shine. By capturing enough network traffic and utilizing brute-force or dictionary attacks, it's often possible to retrieve the WEP key. However – and this is crucial – WEP is outdated. Almost no modern networks still use it because of its significant vulnerabilities. It's like learning how to pick a lock on a door that's already been replaced by something more secure.
6. The Illusion of WPA/WPA2 Security: Authentication Woes
Now, let's step up the security game. WPA and WPA2 are far more robust than WEP. They use stronger encryption protocols, but they're not invincible. The most common weakness lies in the password itself. Many people choose weak, easily guessable passwords. If someone guesses their passwords at random, its called a brute-force attack. WPA/WPA2 is vulnerable to the same types of attack, however, the process is much longer, therefore it's harder to crack.
7. Dictionary Attacks: Where Weak Passwords Fail
A dictionary attack uses pre-compiled lists of common passwords. Imagine trying every possible word in the dictionary to unlock a safe. If you use a common password, you're like leaving your door unlocked! This method is especially effective against users who select easy passwords.
8. Brute-Force Attacks: Guessing Every Possible Combination
Brute-force attacks involve systematically trying every possible combination of characters until the correct password is found. While more effective than dictionary attacks, they are time-consuming, and depending on the complexity of the password, may never even be successful. Like searching for a single grain of sand on an entire beach.
9. Exploiting WPS: The Easy Access Button
Wi-Fi Protected Setup (WPS) was designed to simplify connecting devices to a WiFi network. However, it has some significant flaws when not configured correctly. A PIN, usually 8 digits, is often used to connect a device; it is possible to brute-force this PIN, thereby gaining access to the network’s password. Think of it as a "back door" that’s sometimes left unlocked.
10. Man-in-the-Middle (MITM) Attacks: The Intercept
Man-in-the-middle attacks are where an attacker secretly intercepts the communication between two parties (e.g., your device and the WiFi router). A MITM attacker positions themselves as a gateway and can then steal credentials, read sensitive information, and even inject malicious code. Imagine a sneaky messenger intercepting your mail and changing the contents before delivering it.
11. Evil Twin Attacks: The Phishing Expedition
Evil twin attacks involve creating a fake WiFi network that mimics a legitimate one. The attacker tricks users into connecting to their network. Once connected, the attacker can eavesdrop on all the user's traffic. It's like setting up a deceptive shop next to a popular store!
12. Defending Your WiFi: Security Best Practices
The best offense is a good defense, right? Let’s talk about hardening your WiFi. Use a strong, unique password with a mix of uppercase and lowercase letters, numbers, and special characters. Regularly change your password. Enable WPA2/WPA3 encryption. Disable WPS. Keep your router's firmware updated to patch security vulnerabilities.
13. The Ethics of WiFi Hacking: Responsible Practice
We must always remember that ethical hacking is about gaining knowledge and improving security, not causing harm. We have a responsibility to use this knowledge for good, protecting networks, not exploiting them. Always obtain permission before testing the security of a network you do not own.
14. Legal Implications: What's the Law Say?
Breaking into a WiFi network without authorization is illegal. The legal penalties for network intrusion can range from fines to imprisonment. It's important to understand the laws in your area. So, stick to responsible practices, never break into a network illegally, and stay on the right side of the law.
15. The Future of WiFi Security: A Constantly Evolving Landscape
WiFi security is a constantly moving target. New threats and vulnerabilities will always emerge. It’s a game of cat and mouse. The knowledge we gain today might become inadequate tomorrow. That’s why continuous learning, staying updated, and practicing good cybersecurity habits are essential. We must always keep our digital front yard secure.
Conclusion: Embrace the Learning Curve
So, there you have it. We’ve journeyed through the landscape of WiFi security, revealing the vulnerabilities, the tools and techniques used, and most importantly, the ethical and legal boundaries. We’ve learned how networks operate, and how to build a strong foundation of knowledge. Remember, understanding is the key. We've equipped you with the knowledge to understand the basics and to appreciate the need for strong cybersecurity practices. The world of WiFi is vast, and there is always more to explore. Stay curious, stay safe, and keep learning!
FAQs
1. Is it illegal to try to crack my neighbor's WiFi?
Yes, absolutely. Unauthorized access to any WiFi network is illegal. Even if your neighbor’s WiFi is open without a password, it's generally considered improper to use it without their explicit permission.
2. What are the best tools for protecting your own WiFi network?
The best tools are often the ones built into your router! Enable WPA2/WPA3 encryption, use a strong and unique password, change it regularly, disable WPS, and keep your router’s firmware updated. Additionally, consider enabling a firewall.
3. How can I tell if someone is using my WiFi without my permission?
Most routers have a feature that allows you to see connected devices. Check your router's admin panel to see a list of active devices. If you spot unknown devices, change your WiFi password immediately.
4. Can I get in trouble if I try to "hack" my own WiFi network for educational purposes?
Ethical hacking, even on your own network, carries a degree of risk. Ensure you understand the legal implications in your area. It's always advisable to research the legality behind such activities. Use only tools you have full rights to, and don't engage in any activity that could harm your network or others.
Laptop WiFi Dongle: The SHOCKING Upgrade That Blew My Mind!CRACK WiFi Passwords Explore FERN WiFi Password in 3 Minutes ETHICAL Hacking

By G MAN Security CRACK WiFi Passwords Explore FERN WiFi Password in 3 Minutes ETHICAL Hacking by G MAN Security
2024 New How to Check Wi-Fi Passwords in 2 Minutes Works on Any Laptop Free
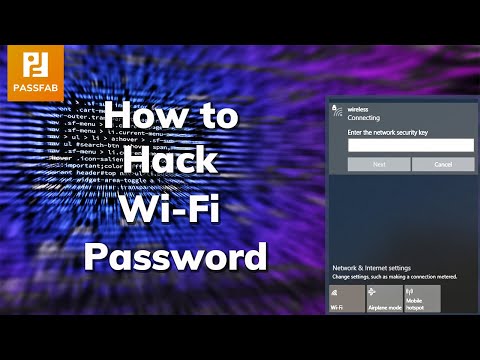
By PassFab 2024 New How to Check Wi-Fi Passwords in 2 Minutes Works on Any Laptop Free by PassFab
How to HACK WIFI How To Hack Wifi Password Wifi Hack Only 5 Mints

By You My Host How to HACK WIFI How To Hack Wifi Password Wifi Hack Only 5 Mints by You My Host

Title: CMD Find all Wi-Fi passwords with only 1 command Windows 10 11 NETVN
Channel: NETVN82
CMD Find all Wi-Fi passwords with only 1 command Windows 10 11 NETVN by NETVN82
Laptop Working
Here's the article:
Unveiling the Secrets of Sustainable Urban Gardening: Cultivating Green Sanctuaries in Concrete Jungles
The relentless march of urbanization has, undeniably, reshaped the landscapes we inhabit. Concrete and steel now define the horizon in many corners of the globe, leaving a pervasive disconnect between humanity and the natural world. However, a burgeoning movement, fueled by a deep desire for ecological harmony and personal well-being, is taking root: sustainable urban gardening. This isn't merely a trend; it’s a powerful reclamation of space, a conscious effort to weave pockets of natural beauty into the very fabric of our cities. We, as stewards of this planet, have a crucial role to play.
Embracing the Principles of Sustainable Urban Gardening: Ecosystems in Miniature
At its core, sustainable urban gardening is a holistic approach. It's about creating self-sustaining ecosystems, miniature versions of the natural world, within the confines of urban environments. This necessitates a profound understanding of ecological principles. This approach encompasses various practices, each contributing to the long-term health of the garden and, by extension, the planet.
One of the primary tenets is water conservation. In urban settings, water is often a scarce resource. The embrace of techniques that minimize water usage is paramount. Rainwater harvesting, by capturing and storing water from rooftops and other surfaces, provides a valuable source of irrigation, reducing dependence on municipal water supplies. Drip irrigation, a system that delivers water directly to the roots of plants, minimizes water loss through evaporation. Selecting drought-tolerant plant species, those that thrive in semi-arid conditions, further contributes to water conservation efforts.
Another critical aspect of sustainable urban gardening is soil health. Healthy soil is the foundation upon which a thriving garden is built. In urban environments, the soil is often compromised, depleted of nutrients, and contaminated with pollutants. Composting offers an elegant solution. By recycling organic waste – kitchen scraps, yard trimmings, and other biodegradable materials – we can create a nutrient-rich compost that enriches the soil, improving its structure and water-holding capacity. Using cover crops, such as clover or rye, can help to prevent erosion, suppress weeds, and add organic matter to the soil when tilled under. The use of organic fertilizers, such as compost tea or fish emulsion, provides plants with essential nutrients without the harmful side effects of synthetic fertilizers.
Finally, sustainable urban gardening emphasizes biodiversity. By nurturing a variety of plant species, we create a more resilient and balanced ecosystem. This attracts beneficial insects, such as pollinators like bees and butterflies, which are critical for pollination and the overall health of the garden. Companion planting, the practice of strategically positioning plants that benefit each other, can further enhance biodiversity. For example, planting basil near tomatoes can deter pests and improve tomato growth.
Transforming Urban Spaces: From Balconies to Rooftops
The beauty of sustainable urban gardening lies in its adaptability. It can be practiced in any urban space, regardless of size or location. From tiny balconies to sprawling rooftops, opportunities abound to create green sanctuaries.
Balcony gardens offer a charming way to incorporate nature into even the smallest living spaces. Container gardening is the primary method used in balcony gardens. The choice of containers is crucial. Choose pots with adequate drainage to prevent waterlogging. Consider the weight of the containers, particularly if you live in an apartment. Select plants that are well-suited to container gardening, such as herbs, vegetables, and compact flowering varieties. Remember to provide adequate sunlight, which varies based on the specific placement of the space.
Courtyard gardens can transform enclosed spaces into vibrant oases of tranquility. Consider the microclimate of the courtyard, taking into account sun exposure, wind patterns, and humidity levels. Design a layout that maximizes the use of space, incorporating raised beds, vertical gardens, and seating areas. Focus on creating a balanced aesthetic, combining ornamental plants and edible varieties.
Rooftop gardens offer a unique opportunity to create significant green spaces in the sky. The challenge is to prepare the roof—ensuring it is structurally sound and properly waterproofed. A drainage system will prevent standing water. Use lightweight growing media to minimize the load on the roof. Choose plants that can withstand the harsh conditions of a rooftop environment, including wind, sun, and temperature fluctuations.
Selecting the Right Plants: A Guide to Thriving in the City
The success of a sustainable urban garden depends heavily on the selection of appropriate plant species. Factors such as climate, sunlight, and available space must be carefully considered.
Herbs are a delightful addition to any urban garden. They are relatively easy to grow, require minimal space, and provide fresh flavors for cooking. Popular choices include basil, mint, oregano, thyme, and rosemary. Herbs thrive in containers and readily adapt to balcony or windowsill settings.
Vegetables can also be successfully cultivated in urban gardens. Compact varieties, such as bush beans, cherry tomatoes, and dwarf peppers, are well-suited to container gardening. Choose vegetables that are known for their resilience. For example, greens such as spinach and kale, which can tolerate partial shade and variations in temperature.
Flowers add beauty and attract pollinators to the urban garden. Select flowers that thrive in your local climate and offer a long blooming season. Consider choosing a variety of colours and textures to create visual interest. Some excellent choices include marigolds, zinnias, petunias.
Combating Pests and Diseases: Natural Solutions for a Healthy Garden
Even in a sustainable urban garden, pests and diseases can pose a threat. However, instead of relying on harsh chemicals, we can embrace natural solutions to maintain a healthy and thriving ecosystem.
Companion planting is a powerful strategy. Some plants naturally repel pests and diseases. Planting marigolds near tomatoes, for example, can deter nematodes, a common tomato pest.
Beneficial insects play a vital role in controlling pests. Attract ladybugs, lacewings, and other beneficial insects by providing them with food and shelter. Consider installing an insect hotel. Use pest-repelling plants, such as sage.
Organic pest control methods are gentle yet effective. Insecticidal soap, made from potassium salts of fatty acids, can control soft-bodied pests. Neem oil, extracted from the neem tree, is a natural insecticide, fungicide, and miticide.
The Benefits of Sustainable Urban Gardening: Beyond the Blooms
The benefits of sustainable urban gardening extend far beyond the aesthetic appeal of a thriving garden. It offers a multitude of advantages for individuals, communities, and the environment.
Health and well-being: Gardening provides a therapeutic outlet, reducing stress and promoting relaxation. The physical activity involved in gardening can improve physical health. Access to fresh, homegrown produce promotes a healthy diet and reduces exposure to pesticides and herbicides.
Community building: Urban gardens often serve as gathering places, fostering a sense of community among residents. They provide opportunities for education, skill-sharing, and social interaction.
Environmental sustainability: Urban gardens reduce the urban heat island effect, mitigating the impact of climate change. They improve air quality. They support biodiversity by providing habitats for pollinators and other beneficial organisms.
Economic benefits: Urban gardens can reduce food costs, particularly for those who grow their own produce. They can create opportunities for local food production and entrepreneurial ventures.
Looking Ahead: The Future of Green in the Urban Landscape
Sustainable urban gardening is not just a passing trend; it is a transformative movement. It represents a shift in our relationship with the natural world, a conscious effort to reintegrate nature into our daily lives. As we continue to grapple with environmental challenges and seek ways to enhance our well-being, the role of sustainable urban gardening will only become increasingly important. Through dedication, ingenuity, and a shared commitment to a greener future, we can transform our cities from concrete jungles into vibrant, thriving green sanctuaries. The journey begins with a seed, a commitment, and a vision of a more sustainable tomorrow. We will continue to advocate for the transformation of urban landscapes. We must cultivate a deeper understanding of the ecological benefits of green spaces while fostering community engagement and promoting mindful practices.
