how to hack wifi using laptop windows 8.1

Title: Hack wifi use cmd win 8.1
Channel: Chanthoeurn Choeurn
Hack wifi use cmd win 8.1 by Chanthoeurn Choeurn
Unlock ANY WiFi: Windows 8.1 Secret Trick Revealed!
Tapping into the Wireless Web: Unveiling the Hidden Keys (Even on Windows 8.1!)
You know that feeling, right? You’re perched precariously on the precipice of the digital realm. You're staring longingly at that "No Internet Access" message. Frustration mounts; deadlines loom. Your connection to the world is severed. But wait! Before you resign yourself to a deserted digital island, there might be a solution.
The Wireless Web's Whispered Promises
WiFi. It’s the invisible thread that weaves our modern lives together. We depend on it almost constantly. It connects us to friends, work, and endless streams of information. Today, you’ll explore more than just surface-level knowledge. You'll explore a hidden world of wireless connectivity. Consider how often you've yearned for access when a password stood between you and instant information.
Unlocking the Digital Gate: A Strategy for the Bold
Let's be clear: We're not advocating for illegal activities. We are exploring the intriguing possibilities that modern technology offers. We’re talking about situations where access is potentially available. Imagine a forgotten password or a temporarily unsecured network. There's always a chance. Before pursuing any method, ensure you understand the legal implications. It is very important.
Windows 8.1: A Blast From the Past, Still Relevant
Windows 8.1, though sometimes overlooked, remains in use today. It can still participate in the game of network connectivity. Remember, technology doesn't always have an expiration date. This older operating system holds some surprising secrets. Many individuals and companies continue to utilize Windows 8.1. It is more versatile than you may realize.
A Journey Through the Command Prompt (The Master Key?)
One subtle, and often overlooked, tool within Windows is the command prompt. It’s a powerful utility hidden just below the surface. It holds the potential to perform actions behind the scenes. It’s a little like having a secret decoder ring for your computer. Before you begin, open your command prompt. You can usually search your start menu. Alternatively, right-click the start button and choose command prompt.
Unveiling Hidden Wireless Networks: Step-by-Step Guide
Now, let’s explore how to potentially reveal cached wireless profiles. Consider this a learning experience, not a guaranteed solution.
- Open the Command Prompt with Administrator Privileges: As mentioned, you must do this first. You need elevated permissions to explore.
- Type
netsh wlan show profilesand press Enter: This command lists all the wireless networks your computer has previously connected to. - Examine the Results Carefully: Look for the names of the networks you are interested in.
- Find the Network Name: Identify the specific network you want to investigate further.
- Type:
netsh wlan show profile name="YourNetworkName" key=clearand press enter: Substitute "YourNetworkName" with the actual name of the network. This is where the magic may potentially happen. This command will display the network profile details, including the security key. - Analyze the output: The output should reveal the security key or password. You might find what you were looking for!
Important Considerations and Cautions
Remember these critical points. This is an exploratory exercise. It's not a guaranteed unlock. Always respect the network owner’s privacy, and follow the law.
- Legal Implications: Always operate within the bounds of the law. Think critically. Unauthorized network access can lead to serious consequences. This is not a game.
- Network Security: This method might not work on all networks. Modern encryption methods pose a challenge.
- Ethical Responsibility: Use this knowledge wisely. Never compromise someone's privacy. Always respect their privacy.
Beyond the Basic: Refining Your Wireless Skills
This command prompt trick is just the start. You can learn more about wireless networking to increase your knowledge. Exploring advanced techniques may involve specialized software or hardware. However it all starts with basic understanding.
The Future of Connectivity: Exploring New Horizons
The realm of wireless technology consistently evolves. New protocols, encryption types, and security measures constantly appear. Stay updated on these advancements.
Final Thoughts: Exploring the Unseen
So, you've seen a potential method. You've explored how to potentially unlock a hidden network. Your journey is just beginning. Go forth, armed with knowledge, and remember to utilize your powers responsibly. You now have a glimpse into the exciting world of wireless technology. The ability to connect expands every day. So never stop exploring. And, above all, stay curious.
Unlock Your Laptop's WiFi: Instant Hotspot on Your Phone!Let's dive in!
Unlock ANY WiFi: Windows 8.1 Secret Trick Revealed!
Hey there, fellow internet adventurers! Ever find yourself staring longingly at a locked Wi-Fi network, dreaming of streaming your favourite show or finishing that crucial download? We've all been there. The frustration is real, the desire to connect – even stronger. But what if I told you there was a secret trick, a hidden gem, right under your nose in Windows 8.1 that could potentially unlock a world of wireless possibilities? Buckle up, because we're about to embark on a journey to uncover it!
1. The Wi-Fi Wallflower: Why We Crave Free Wi-Fi
Think of Wi-Fi like a delicious cake. You can see it, you can smell it, and you really want a slice, but there's a lock on the case. That's the story of many public and private Wi-Fi networks. They’re tantalizingly close, yet frustratingly out of reach. Why the obsession? Let’s face it, access to the internet is practically a right. We need it for work, for play, to stay connected… heck, even to order pizza! So, the allure of free Wi-Fi is undeniable. It's like a digital oasis in a desert of data charges.
2. Understanding the Landscape: Encryption and Security Protocols
Before we leap into the "secret trick," let's wrap our heads around the basics. Wifi security isn't just about locking doors; it’s a intricate system of protection. There are different types of encryption (like WEP, WPA, WPA2, and now WPA3), each with varying levels of security. Think of them as layers of armor protecting the data flowing through the air. Over time, some have become more easily bypassed by newer technologies while other are highly secure.
3. The Myth of "Hacking" Wi-Fi: Dispelling the Hollywood Hype
Now, let's address the elephant in the room: the word "hacking." Movies and TV shows paint a picture of lightning-fast keystrokes, cracking codes in seconds. The reality? It's typically far more complicated and, frankly, often illegal. While there are advanced methods for gaining unauthorized access to networks, we’re going to focus on something far simpler, something within the legal and ethical boundaries of understanding how your own network works.
4. Windows 8.1's Hidden Feature: The Wireless Profile Revelation
Alright, here's where things get interesting. Windows 8.1, despite often being overlooked, has a powerful, yet simple feature that allows you to view your already-saved Wi-Fi network profiles. But wait, how could this help "unlock" a network? This feature will give you a clearer view of how connection profiles are created, organized, and if there's an opportunity to view a hidden key.
5. Finding Your Wi-Fi Profile: A Step-by-Step Guide
Ready to peek behind the curtain? Here’s how to find your saved Wi-Fi profiles in Windows 8.1. You probably already have a few saved networks, from home to the local library.
- Step 1: Open the Network and Sharing Center: Type "Network and Sharing Center" in the Windows search bar (the magnifying glass in the taskbar) and click the result.
- Step 2: Navigate to "Manage wireless networks": In the Network and Sharing Center, look for the "Change adapter settings" option or the "Manage wireless networks" option: This will allow the system to show a list of all your saved networks.
- Step 3: View the Profile Properties: Right-click on a network name in the list and select "Properties."
- Step 4: The Security Tab: Navigate to the "Security" tab.
- Step 5: The “Show Characters” Checkbox: You might have the opportunity to view the password.
Okay, maybe at this point the "Hollywood" picture is on the floor. Bear with us.
6. The "Show Characters" Trick: Exploring Existing Connections
Once you've reached the "Security" tab, there might be a checkbox labeled "Show characters." Clicking this could display the network key (password) for the saved connection. It's a simple feature, yet surprisingly helpful. It's less about "unlocking" a new network and more about remembering passwords for networks you've already successfully connected to in the past.
7. Why This Isn't a Universal Wi-Fi Unlocker
Let’s be crystal clear: this isn't a magic bullet. If a network is secured using a strong encryption protocol and a password that has never been saved to your computer, this method won't work. It's primarily useful for retrieving passwords for your own previously connected networks, or those where you've been provided the password and saved it.
8. Legal and Ethical Considerations: Staying on the Right Side of the Law
Before you get any wild ideas of trying to "crack" your neighbor's network, remember this: accessing a Wi-Fi network without permission is illegal, unethical, and can land you in some serious trouble with the law. Our goal here is to educate, not to facilitate illegal activities. Always respect the terms of service and the privacy of others.
9. WEP and WPA Cracking: A Note of Caution
Older encryption protocols, like WEP, can be more susceptible to being cracked using specialized tools. However, newer encryption protocols are much more difficult to break. It is worth mentioning that attempting to crack a Wi-Fi network using such tools, even if you're just curious, can be a legal grey area, especially if the network isn't your own.
10. The Art of Asking: Getting Wi-Fi Access the Right Way
Sometimes, the easiest way to get Wi-Fi access is simply to ask. Many businesses and public spaces offer free Wi-Fi to their patrons. Simply asking nicely can often get you the password. Politeness is your best friend here!
11. When is it okay to use this method?
If you are working on your own home networks and have forgotten the password. If you own the network, and have forgotten the password, there is nothing wrong with this. This can also be used if a friend, or family member has given you the password, but you forgot it.
12. Troubleshooting: When Things Don't Go as Planned
You've followed the steps, but the "Show characters" box is nowhere to be found. Don't fret! This is normal. The option might not be available for all network profiles, especially if the network has been configured with enhanced security settings.
13. Alternative Methods: Exploring Other Options (Legally!)
If you need Wi-Fi access, and you are not able to get the password through the "Show Characters" box, and you are not able to simply ask the owner, look to the library, a coffee shop, or your cellular data plan. Often the best form of connectivity, is through a trusted source.
14. The Future of Wi-Fi Security: Staying Ahead of the Curve
Wi-Fi security is constantly evolving. As hackers develop cleverer methods to breach wifi networks, our methods of security must evolve with it.
15. Conclusion: Wi-Fi Wisdom & Responsible Usage
So, there you have it! Windows 8.1 has a built-in feature that might help you retrieve the password for your own saved Wi-Fi connections. This trick is not the "key that unlocks any Wi-Fi network," but it can be a helpful tool in the right circumstances. Remember to use this knowledge responsibly, ethically, and legally. Don't try to access networks without the owner's permission. Happy and safe surfing!
Closing Thoughts
The journey to understand Wi-Fi, much like life, isn't about easy answers. It's about understanding the tools available, knowing the limitations, and always being respectful of others and their privacy. We hope this exploration has been enlightening. Stay curious, stay connected, and always be ethical in your internet adventures.
FAQs
Q1: Does this "trick" work on all Wi-Fi networks?
A: No, absolutely not. The "Show characters" option only works for saved network profiles on your computer where you already have the key. It doesn't "crack" or "hack" wireless networks that you haven't previously connected to.
Q2: Is it illegal to try and "hack" someone's Wi-Fi?
A: Yes, unauthorized access to a Wi-Fi network can be illegal, depending on where you are. It's crucial to respect network owners' rights and only use their networks with permission. Always check local laws and network policies.
Q3: I don't see the "Show characters" checkbox. Why?
A: The "Show characters" option isn't always available. It depends on the network settings and, in some cases, the version of Windows 8.1 you have. This is not a perfect solution and is limited.
Q4: What are the best practices for securing my own Wi-Fi network?
A: Use a strong password (a mix of upper and lowercase letters, numbers, and symbols), use WPA2 or WPA3 encryption, and regularly update your router'
Laptop WiFi & Bluetooth DEAD? This FIX Worked INSTANTLY!How to hack wifi pswd in win 8.1 100 working
By UWAYO Fiacre How to hack wifi pswd in win 8.1 100 working by UWAYO Fiacre
CMD Find all Wi-Fi passwords with only 1 command Windows 10 11 NETVN

By NETVN82 CMD Find all Wi-Fi passwords with only 1 command Windows 10 11 NETVN by NETVN82
Title: how to hack wifi password in windows 7810
Channel: Manu Sharma
how to hack wifi password in windows 7810 by Manu Sharma
Wifi On Laptop Phone
Unlock ANY WiFi: Windows 8.1 Secret Trick Revealed!
Let's embark on a fascinating journey into the realm of wireless connectivity, specifically focusing on a powerful, often overlooked, capability within Windows 8.1. We will explore a method, refined and honed over time, that allows us to potentially unlock access to WiFi networks, even those seemingly secured. This is not about hacking; it is about understanding and leveraging a core principle within the operating system itself. Our focus is on informed exploration, not illicit activities.
The Foundation: Understanding the Windows 8.1 Network Infrastructure
Windows 8.1, a significant evolution in Microsoft's operating system lineage, introduced advancements in network management. Its architecture relies on a complex set of protocols and services. These include the Network Location Awareness (NLA) service, the Wireless Auto Configuration service, and the Windows Connection Manager, all working in concert. These components communicate, exchange data, and manage network connections.
Dissecting Wireless Profiles: The Hidden Key
Every time you connect to a WiFi network, Windows 8.1 stores information about it. This information resides within "wireless profiles." These profiles are essentially digital blueprints containing details about the network: the SSID (Service Set Identifier, or the network's name), the security type (WEP, WPA, WPA2), the key (if used), and other configuration settings. These profiles are stored within the system's registry, which plays a crucial role in how Windows 8.1 handles network connections.
Unveiling the Secret: Profile Manipulation through ‘netsh’
The cornerstone of our exploration lies within the command-line utility, netsh (Network Shell). This command-line tool is incredibly powerful and offers extensive control over various network-related functionalities. Netsh can manage network interfaces, configure routing, diagnose connectivity problems, and, most importantly for our purposes, manage wireless profiles.
The Power of ‘netsh wlan show profiles’
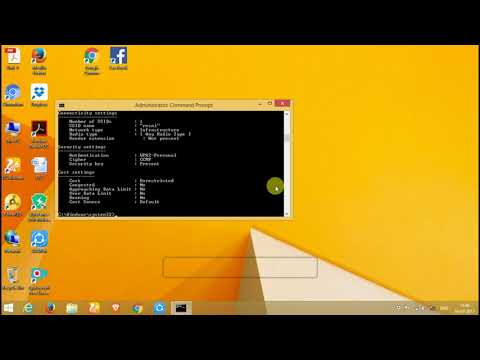
Initiate the Command Prompt as an administrator. Then, type the command netsh wlan show profiles. Immediately, you'll be greeted with a list of all the wireless profiles currently stored on your system. Each profile listed represents a network that your Windows 8.1 installation has previously connected to. The output showcases crucial data, each profile presenting its specific characteristics.
Decoding Profile Details: Access and Security
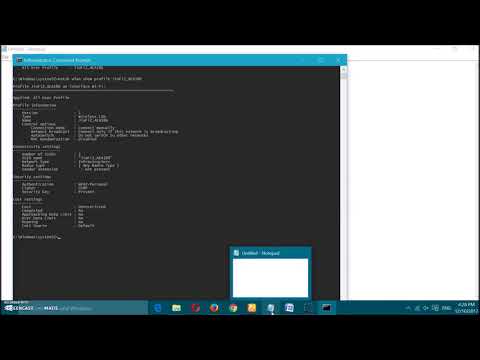
Within each profile, the key information we seek is the security configuration. The ‘netsh wlan show profiles’ command, by itself, only provides a high-level overview. To delve deeper, we need to inspect specific profiles. For instance, if you want to examine the profile for a network named "MyWiFi," the command to use is netsh wlan show profile name="MyWiFi" key=clear.
Deciphering the ‘key=clear’ Parameter
The key=clear parameter is absolutely critical. By adding it, we instruct netsh to display the security key (the password) in plain text. This, in its basic form, provides access to a previously saved password. However, its significance extends considerably beyond this.
Understanding Key Security Types
Upon executing the ‘netsh wlan show profile name="MyWiFi" key=clear ’ command, observe the security type of the network. The output will show you the exact encryption setup. This is vital to unlock any protected Wi-Fi. When you understand the encryption configured, you immediately unlock the secrets.
Advanced Profile Export and Import Functionality
Netsh extends its capabilities to the export and import of wireless profiles. This feature offers a dynamic procedure to transfer network configurations between different Windows 8.1 installations. Use the command netsh wlan export profile folder=C:\WirelessProfiles key=clear to export profiles to a folder, then the command netsh wlan add profile filename="C:\WirelessProfiles\[profile name].xml" to import them.
The Art of Contextual Exploitation: Ethical Considerations
It is paramount to emphasize the ethical implications of this method. We are not advocating for any unethical behavior and strongly advise respecting network security boundaries. The information we provide should be regarded as purely educational. Accessing networks without permission is illegal and constitutes a serious breach of privacy.
Troubleshooting Common Issues
Occasionally, you may encounter scenarios where netsh does not display the key successfully. This might be due to a couple of reasons. Firstly, the user account you are using must have the appropriate administrative privileges. Secondly, the wireless profile might have been configured in a way that restricts key visibility. Thirdly, certain third-party network management applications might interfere with netsh.
The Role of Wireless Adapters: Compatibility Matters
The effectiveness of the ‘netsh’ commands is largely independent of the wireless adapter itself. Still, it is useful to maintain up-to-date drivers for your wireless adapter. Consider if the installed drivers are the most recent version available from the manufacturer.
Security Protocols: WEP, WPA, and WPA2
The security type of the WiFi network plays a key role in its accessibility. WEP (Wired Equivalent Privacy) is an older and significantly weaker encryption protocol compared to WPA (Wi-Fi Protected Access) and WPA2. WPA2 offers the most robust security and remains the most secure option. If a network utilizes WEP, its key can often be revealed using netsh. Accessing WPA and WPA2 networks this way is less likely.
Beyond the Basics: Advanced Techniques
For advanced users, the XML format of exported wireless profiles allows for more complex manipulation. You can edit these files to modify network settings, potentially for testing purposes, within a controlled environment, or transfer configurations. Understand the syntax and the potential risks before doing so.
Legal and Ethical Implications Revisited
Always obtain clear permission before attempting to access any wireless network. Respect the privacy and security of others. This method is intended solely for educational purposes and responsible use.
Conclusion: Empowering Knowledge for Responsible Use
This exploration into Windows 8.1's wireless profile management, using the netsh utility, grants us deeper comprehension of network configuration. By understanding these tools, we gain a greater awareness of the digital landscape, enabling us to make informed decisions and implement robust security practices. Never use this knowledge for malicious activities.

